Should You Choose Asymmetric or Symmetric Data Encryption?
Author: Tatiana Salamanca, MILL5
Date: November 28, 2022
It is very common to hear about message encryption or end-to-end encryption, but what are these? They are both ways to keep your information secure as it is transmitted across systems. There are two types of data encryption – asymmetric and symmetric – each having their own benefits depending on your situation and need. The main difference between each is how the data is decrypted. Let’s discuss the advantages and disadvantages of asymmetric and symmetric data encryption.
Asymmetric Encryption
The Asymmetric Encryption is an encryption method performed with a public key, while the decryption is done with a private key. Let’s explain how this would work. The public key is shared with the sender of the message, which encrypts the message and sends it to the receiver (owner of the public key). The receiver then uses a private key to decrypt the message.
The most common methods that use this encryption method are:
- RSA: a popular algorithm and cryptosystem used to encrypt data with a public key and decrypt it with a private key to transmit the data securely.
- Public Key Infrastructure (PKI): a way to manage encryption keys by issuing and managing digital certificates.
Advantages
- The private key is not shared.
- It is compatible with digital signatures.
- The veracity of the message is guaranteed (i.e., the message is not modified along the way).
Disadvantages
- It consumes a lot of resources and time.
- No possibility of recovering the private key.
- The two parties involved in this encryption method must have knowledge of the implementation process to create the key pairs.
Example RSA C#
In the following post you can find out how to implement an asymmetric encryption with RSA
RSACryptoServiceProvider Class (System.Security.Cryptography) | Microsoft Learn
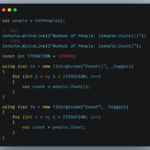
This is the result of the implementation of the code:
Considerations for Asymmetric Encryption
OAEP: Optimal Asymmetric Encryption Padding
RSACryptoServiceProvider.ExportParameters(): This method exports the RSA parameters. If you put true, this method includes private parameters.
RSACryptoServiceProvider.ExportParameters(false);
RSACryptoServiceProvider.ExportParameters(true);
Symmetric Encryption
In the Symmetric Encryption method, the encryption and decryption are performed with the same key, which implies sharing the secret key with the sender. This key is usually also sent encrypted so as not to expose the information.
The most common methods using this encryption are:
- Data Encryption Standards (DES): a low-level block cipher algorithm that converts plain text into 64-bit blocks and converts them into ciphertext using 48-bit keys.
- Triple DES: executes DES encryption three different times in which the data is encrypted, decrypted, and then encrypted again.
- Advanced Encryption Standard (AES): often referred to as the gold standard for data encryption and is used worldwide as the U.S. government standard.
- Twofish: is considered one of the fastest encryption algorithms and is free to use.
Advantages
- It is easy to implement.
- Has a faster learning curve than asymmetric encryption.
- Faster and less resource intensive.
Disadvantages
- It is necessary to share the secret key with the other party involved.
- If someone not involved in this symmetric process guesses or intercepts the secret key, your messages or information will be exposed or compromised.
Example AES C#
In the following post you can find out how to implement a symmetric encryption with RSA
Aes Class (System.Security.Cryptography) | Microsoft Learn
This is the result of the implementation of the code:
Considerations for Symmetric Encryption
Key: it is the secret key to perform encryption and decryption.
Initialization Vector (IV): Symmetric Encryption is a 16-byte Initialization Vector. Typically, this value is sent together with the ciphertext since it is not a secret key. This to guarantee that the same Initialization Vector is used in the encryption and decryption since the Aes class, by default, has a key and an IV when the instance is created.
As we have discussed, different encryption options are available to provide secure and modern information management. Depending on the needs and different scenarios, the most suitable and optimal encryption method can be chosen to best fit your business requirements and resources available. Should you have further questions or need assistance with determining which encryption method is best for your business, please schedule a complimentary Strategy Session with MILL5 by clicking here.
Next up: Outsourcing QA – Benefits, Reasons to Do it & Best Practices